|
|
Identity and Access Management (IAM) Services PEAK Matrix® Assessment 2023
PEAK Matrix® Report
19 Jul 2023
by
Kumar Avijit, Arjun Chauhan, Prabhjyot Kaur, Nishit Meswani
The demand for Identity and Access Management (IAM) services in the global business landscape is accelerating due to digital transformation trends, the importance of data protection, and the complexities of managing IT environments. The need for effective IAM solutions has intensified with the implementation of BYOD (Bring Your Own Device) policies, cloud-based services, and the ongoing cyber threats.
To address the shortage of in-house IAM expertise, companies are adopting external IAM services. This allows organizations to reduce CAPEX and OPEX associated with maintaining an internal IAM team while ensuring efficient and secure management of digital identities. Additionally, as governments worldwide enforce stricter data protection and security regulations, enterprises face pressure to comply with these regulations and adhere to localized data privacy laws. Examples include Europe’s GDPR, California’s CCPA, and Brazil’s LGPD, reflecting the evolving regulatory landscape. Consequently, global enterprises are seeking providers capable of delivering sophisticated, adaptable, and globally compliant IAM services. Key areas of interest include user authentication and authorization, centralized IAM operations, integration of IT/OT IAM services, and regulatory compliance assessments.
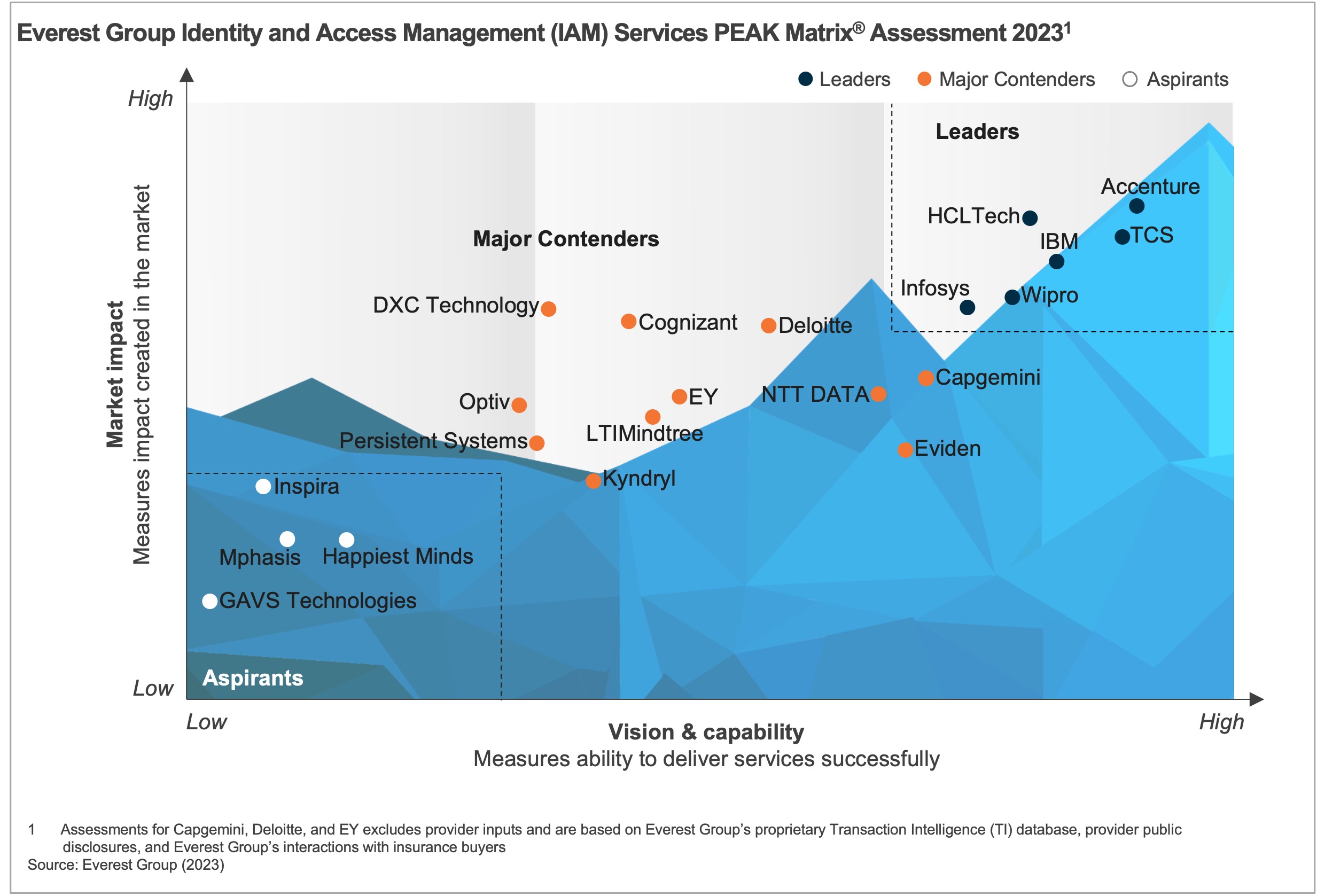
In this report, we present a comprehensive analysis of 21 global IAM service providers as featured on the IAM Services PEAK Matrix® Assessment 2023. The research will help buyers select the right-fit provider for their needs, while providers will be able to benchmark themselves against each other.
Scope
- All industries and geographies
- Services: IAM
- The assessment is based on Everest Group’s annual RFI process for the calendar year 2023, interactions with leading IAM service providers, client reference checks, and an ongoing analysis of the IAM services market
Contents
In this report, we examine:
- IAM services PEAK Matrix® characteristics
- Enterprise sourcing considerations
- Providers’ key strengths and limitations
Membership(s)
Cybersecurity
Sourcing and Vendor Management
Page Count: 46
|
Other Users Also Viewed
PEAK Matrix® Report
25 Jul 2023
In the continuously maturing cloud adoption landscape, enterprises are leveraging cloud services to increase operational efficiency, enable business innovation, and accelerate organizational growth. As economic headwinds challenge organizations, they…
|